The IoT market within finance is expected to triple by 2020.
However, with the rising popularity of the Internet of Things (IoT) and Big Data, banks and insurance firms must prepare themselves for a new wave of security challenges.

The IoT market within finance is expected to triple by 2020.
However, with the rising popularity of the Internet of Things (IoT) and Big Data, banks and insurance firms must prepare themselves for a new wave of security challenges.
The IoT market within finance is expected to triple by 2020.
However, with the rising popularity of the Internet of Things (IoT) and Big Data, banks and insurance firms must prepare themselves for a new wave of security challenges.
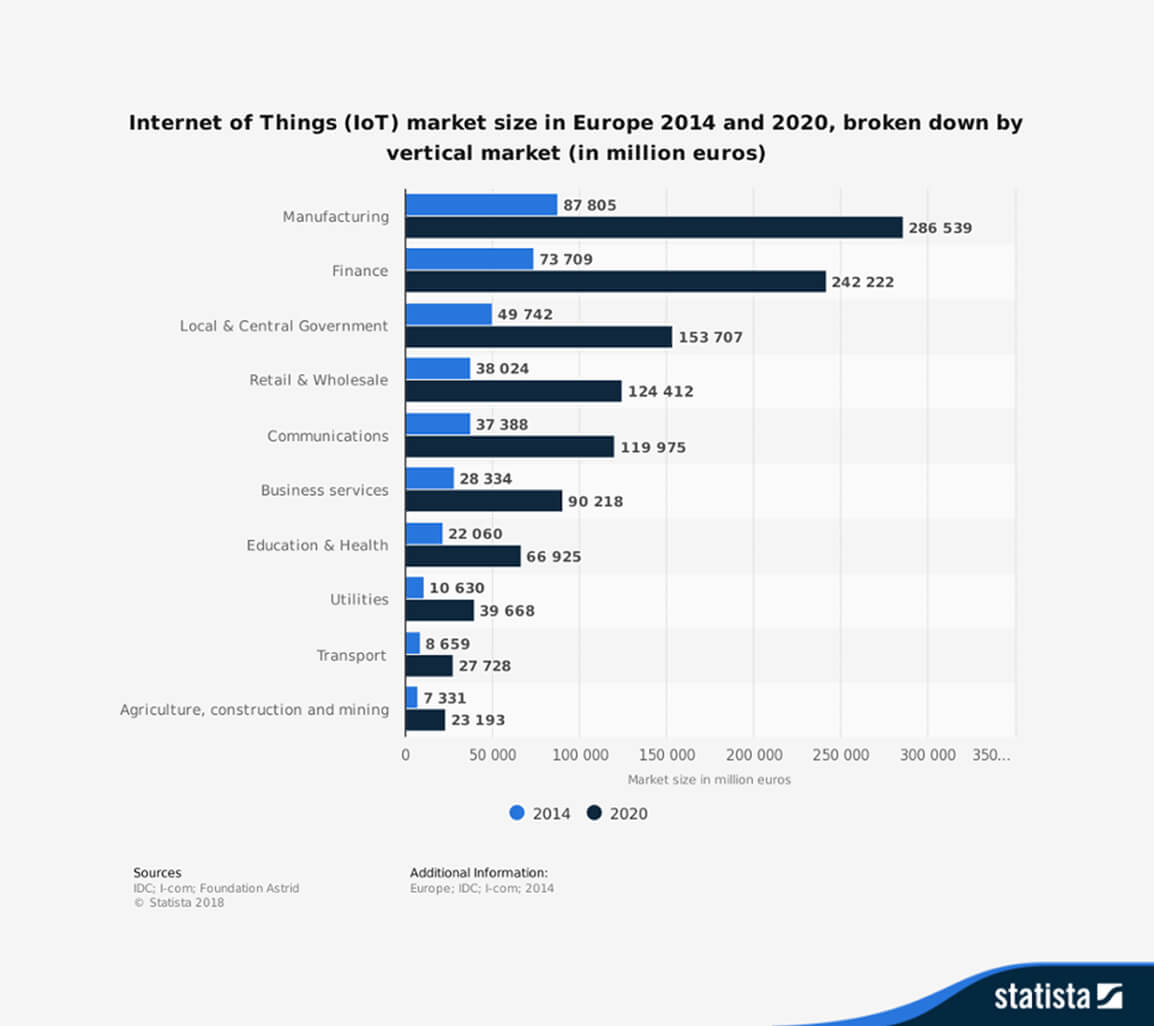
The Internet of Things market is expected to reach €242,222 million in finance by 2020
Financial services firms are twice as likely to experience security incidents than other industries, according to PWC, with cybercrime the second most reported economic crime of all.
But a new challenge doesn’t necessarily mean a new roadblock. With the right security framework, financial organisations can mitigate potential threats and continue to accelerate business growth without fear of losing steam.
Before we get into the technical details, let’s examine two real-life IoT security breaches that have had detrimental effects on mainstream businesses.
In 2016, an Internet of Things ‘botnet’ took advantage of vulnerabilities within TV cameras and routers. After scanning the internet for Telnet ports, the bot used the device’s 61 default credentials to force-hack its way into the network.
By the end of November 2016, it’s thought that 900,000 routers from Deutsche Telecom were compromised, leaving users unable to access the internet. Although this particular attack was confined to internet-connected TV cameras and routers, brute-force attacks can affect any other IoT device.
Car technology is advancing every day. So much so, that Ford Motors are expecting to offer driverless vehicles to the public by 2025.
But although these larger-scale IoT devices will provide a new level of convenience for users across the world, without the right security measures they could become a potential threat.
Poorly secured connected cars are potential targets for hackers before they even leave the warehouse. Even at this stage in the manufacturing process, companies need to work with security in mind. If a hacker discovers a loophole within the IoT network, they could take control of the car’s functionality.
This scenario was role-played at the 2016 Black Hat conference. Although it was extremely difficult to hack into the car’s network, Chris Valasek and Charlie Miller were able to control a Jeep Cherokee’s speed and brakes.
As well as putting customers in danger, this also has an impact on car insurance policies.
Investing in a secure IoT solution is the only way to avoid these issues. But how do you know what to look for?
We’ve already discussed a few examples of IoT breaches. But now let’s look at what your business can do to prevent these issues from occurring.
IoT security challenges don’t just concern your in-house team; they impact your customer too. And, worryingly enough, half of financial firms in the US have experienced an IoT attack.
Some of the main IoT security concerns experienced by consumers are:
Fortunately, with the right mindset and technology, your business can overcome IoT security challenges and ensure both your business and customers are safe.
With that in mind, let’s take a look at the five most prominent IoT security challenges facing FSI and what your organisation can do to tackle them.
IoT technology requires a shift in mindset, particularly for devices that hold important financial and personal information.
However, not all IoT devices are secure enough to prevent identity theft and security breaches.
For instance, only 50 percent of smart watches allow users to set a pin code or pattern. What’s more, 87 percent of enterprises worry about vulnerabilities within the IoT devices themselves.
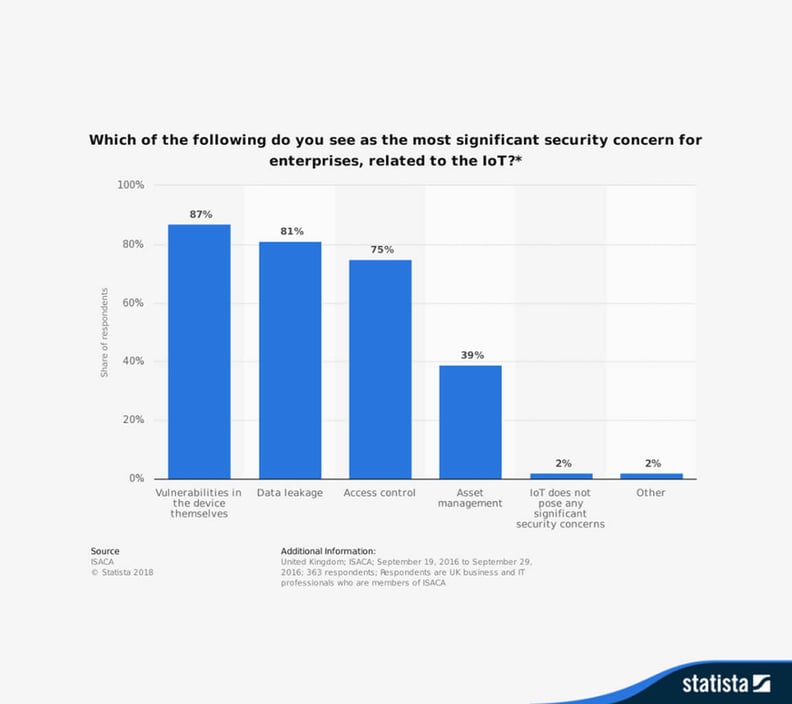 87 percent of enterprises are concerned about vulnerabilities in IoT end-devices.
87 percent of enterprises are concerned about vulnerabilities in IoT end-devices.
Biometric authentication, such as fingerprint scans and voice recognition, can provide a safer way of securing data, using tech that is already familiar to many mobile phone users. But, if you’re unable to implement biometric functions, Azure’s multi-factor authentication can also provide multiple layers of security, leaving your data protected.
A lost payment device (such as a smart watch or mobile phone) poses far less of a threat when the financial information it contains is locked and encrypted. Implementing geolocation functions allows users to track their device’s location in the event they’re stolen or lost.
This keeps your customers’ credentials secure, as well as sealing off any back doors to your business, which could result in data breaches and reputational damage.
But, of course, even with increased security at the end-user level, hackers can still infiltrate your network or data centre.
One of the biggest IoT security challenges for smart devices is also a common threat to all software deployments:
Inefficient patching.
Outdated devices may contain dangerous bugs or vulnerabilities that hackers can target and therefore pose a risk to your organisation’s data security.
Whether you’re patching in-branch IoT devices or customer wearables, it’s important to monitor and test the stability of each update (and device models) to ensure their security posture is watertight. Since, customers can always opt-out of updates, consider enrolling automatic updates or retiring outdated models.
Azure’s IoT solutions closely monitor your assets with bidirectional communication. This means that your business can remotely understand the state of each device and send out update or notification commands accordingly.
The Mirai botnet hacking shows just how important passwords are to IoT networks and the kinds of IoT security challenges your business could face.
A recent government report recommends that vendors don’t sell IoT devices with default credentials (such as the username ‘admin’). However, these are only guidelines and manufacturers don’t necessarily have to follow them.
Weak login details leave your financial IoT devices vulnerable to brute-force attacks. So, unless you want to follow in the steps of companies like Mirai, it’s vital you either change the default settings of your devices before you deploy them. Without the right security measures, you’re putting your business assets and customer information at risk.
Fortunately, tool such as Azure Active Directory help to tackle unauthorised access to connected devices. Using cloud intelligence, Active Directory’s ‘smart lockout’ detects common brute-force techniques and attempts to guess device passwords. By identifying invalid users, the tool locks out potential hackers, whilst verifying the identity of all authorised users.
It’s vital you invest in the appropriate safeguarding measures when processing IoT data. If you’re a financial organisation that processes masses of sensitive data, one breach could potentially ruin your reputation and customer trust.
Although keeping your IoT data in sight seem to offer an added sense of physical security, processing your information on-premise is a big IoT security challenge. Without the right expertise or physical hardware, compromised or stolen infrastructure puts you at great risk.
By processing your IoT data in the cloud, you stand a much better chance of keeping your assets secure. Azure Active Directory, for example, uses user authentication and authorisation to prevent unauthorised persons from accessing your IoT data. You can use this functionality to split the IoT data processing journey. This allows you to tailor who has access to the data at each point in its lifecycle.
More than 70 percent of financial organisations admit that the rapid deployment of new technologies - such as the cloud, big data and IoT – is a larger priority than securing their infrastructure and network.
But, while the Internet of Things is a trending business investment for financial organisations, it should never come at the expense of weakened defences. To keep your business and customers safe, you need to place security at the heart of your investments, ensuring you keep IoT security challenges in mind across all layers of your network:
Investing in a compliant, transparent and secure IoT hub, on a safe platform like Azure, can ensure your data remains safe throughout your Internet of Things journey and can allow you to detect threats before they cause irreversible damage.
Azure’s solution allows you to secure and manage billions of different IoT devices, with functions such as applying identities and credentials to individual devices.
With built-in cloud security, your IT team spends less time on routine patching and monitoring and more time analysing IoT data for business-driven insights.
So, to summarise:
While IoT creates new entry points for hackers to exploit, a holistic approach to security helps prevent leaks and weaknesses. In fact, financial firms who haven’t experienced IoT data breaches spend 65 percent more on IoT security than those who have.
As long as companies continue to look at security as a ‘feature’ rather than as a fundamental operating characteristic, they will be unable to cooperate to build proper security infrastructure
Building cloud architecture with proactive defences in mind makes it easier to integrate game-changing technology and create IoT solutions that not only drive better business outcomes, but maintain high-quality data security.
Topics: Financial Services, Big Data, IoT
The IoT market within finance is expected to triple by 2020.
However, with the rising popularity of ... >
Eagle House, 167 City Road,
London, EC1V 1NR